A lot of network services run using Transmission Control Protocol or TCP as the transport layer protocol. This is because TCP offers connection-oriented communication which allows the transmitting device to be sure that the intended recipient of the message actually receives it, because a two-way connection is created.
Not every application needs to have that sort of connection, however, especially real-time applications where it’s preferable that a message is dropped rather than having to wait for it to be re-transmitted, delaying everything else. For these applications, the User Datagram Protocol or UDP transport layer protocol is generally used.
One example of a type of program that uses UDP is online video games. These games rely on constant updates sent by the server and computer and any delay caused by having to retransmit data is significantly more disruptive than having to deal with a missed packet or two.
As these UDP based services can be on any network, it is important to check for them as part of a penetration test. Thankfully as UDP is pretty common it’s generally supported by network testing software, and Nmap is no exception.
How to scan UDP ports with Nmap
Testing UDP ports with Nmap is very similar to testing TCP, in fact, the syntax is essentially identical. The only difference is that you need to specify the “scan type” flag as “-sU” rather than “-sT” or “-sS”. For example, a command could be “nmap -sU 127.0.0.1 –top-ports 100 -vv” to scan the loopback address for the top 100 most common UDP ports and to report the results with doubly verbose output.
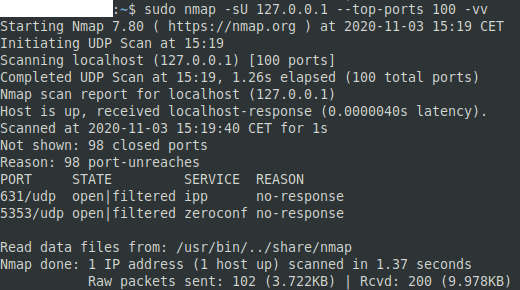
One thing to be aware of with a UDP scan is that it will take a long time. Most requests do not receive any response, meaning the scan has to wait for the request to timeout. This makes scans a lot slower than TCP scans which will typically return some sort of response even if a port is closed.
There are four results you can see for UDP ports “open” “open|filtered”, “closed”, and “filtered”. “Open” indicates that a request got a UDP response. “Open|filtered” indicates that no response was received, which could indicate that a service was listening or that there was no service there. “Closed” is a specific ICMP “port unreachable” error message. “Filtered” indicates other ICMP unreachable error messages.