One of the many tools built-into Burp Suite is “Repeater”. Repeater is designed to take requests that you’ve made and to be able to edit and replay them at will. It is a very useful tool for tweaking and refining payloads designed to exploit Cross-Site Scripting or SQL injection vulnerabilities, also known as XSS and SQLI respectively.
How to use Burp Suite Repeater
The first thing you need to do with Repeater is to send it a request. To do so, find a request that you want to use in the Target, Proxy, Intruder, or even the Repeater tab, right-click on it, and select “Send to Repeater”. This will copy the request and all related connection information to Repeater, so it is ready to use.

In the Repeater tab, you’ll now be able to find the request that you sent. You can make any changes you want to the request in the “Request” half of the page. Once you’ve made the changes you want to, click “Send” in the top-left corner to send your request. You can find the response in the “Response” column on the right.

Some requests may receive a redirection response rather than an actual webpage response. You can choose to follow the redirection in Repeater by clicking the “Follow redirection” button, that can be found to the right of the “Send” button when there is a redirection to follow.
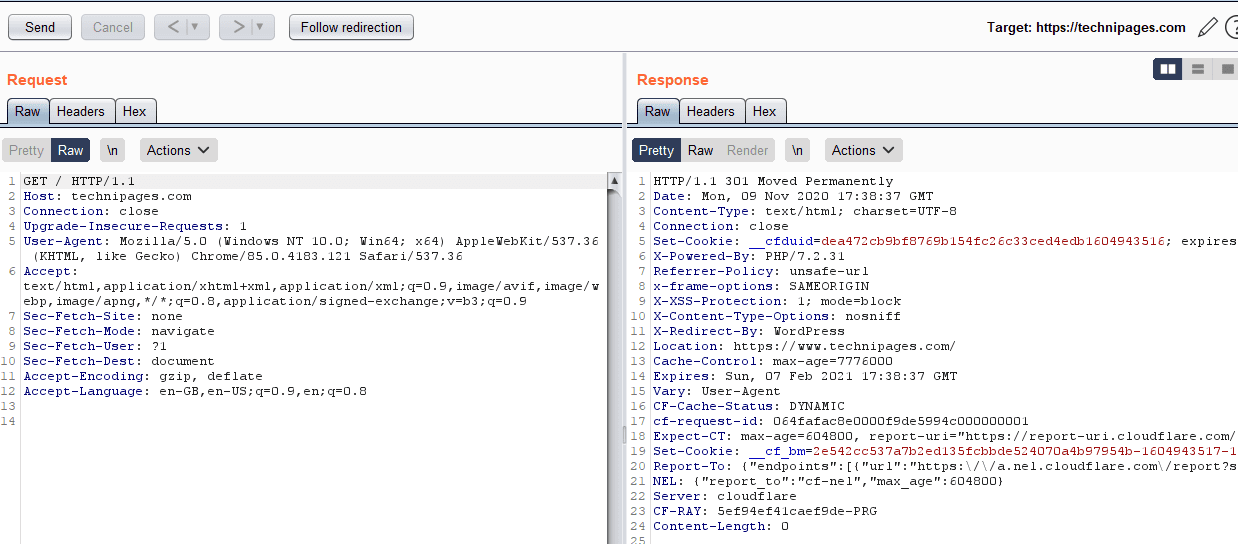
You can use the back and forwards arrows to switch back to earlier requests if you decide that your incremental changes to the request aren’t working as intended.
You can manage multiple requests in the Repeater tab via the sub-tabs. If you send a second request to Repeater it will automatically be opened in a new sub-tab. This can be used to manage multiple different requests or to save a successful request that you want to tweak further. You can re-open a closed sub-tab by right-clicking on the sub-tabs and clicking “Reopen closed tab”



