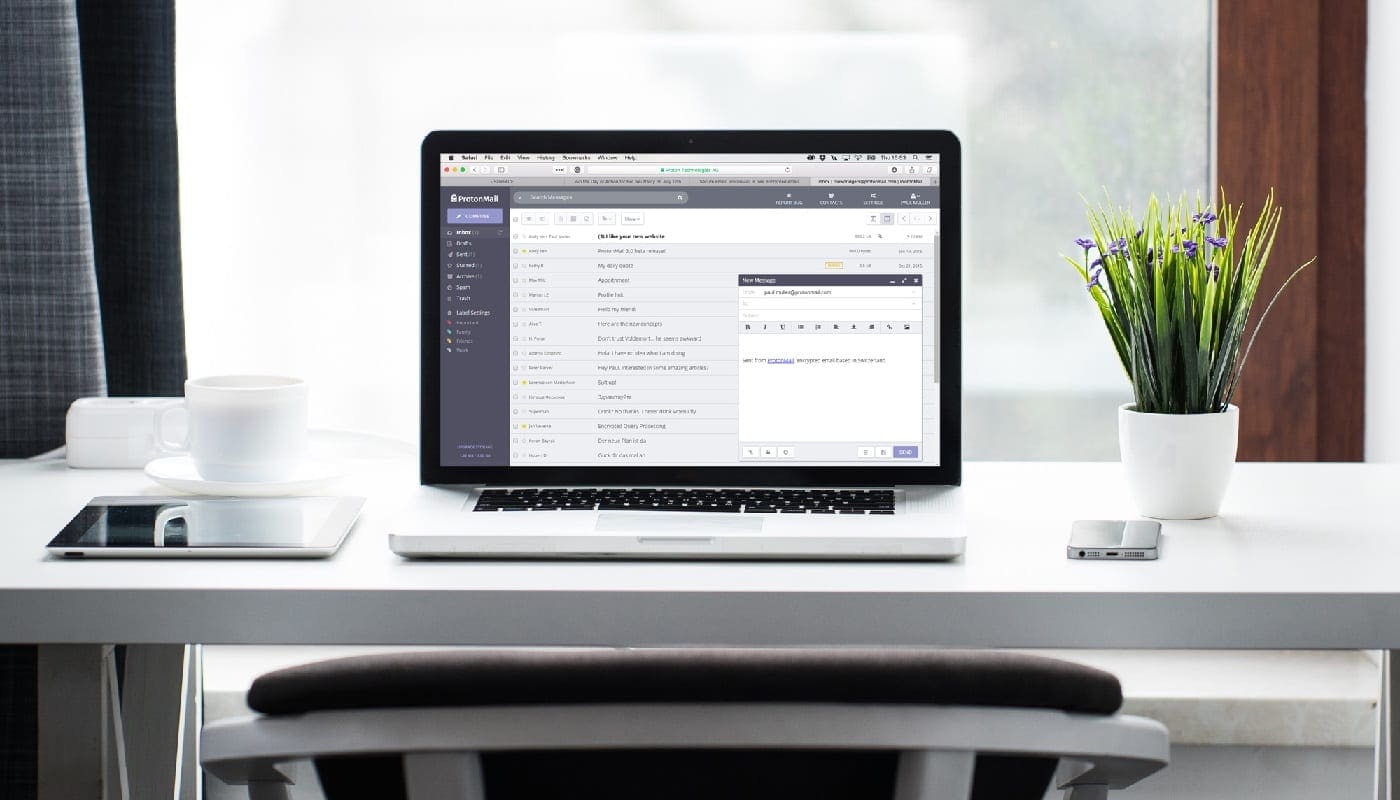
ProtonMail is an email platform run by a Swiss company called “Proton Technologies AG”. It offers an email application for the web and for mobile platforms. The main application is free to access and use, it comes with 500MB of email storage and a limit of 150 emails per day. There are two tiers of paid plans as well as a corporate package.
The “Plus” tier costs 4 Euros, US Dollars, or Swiss Francs a month when billed annually, and offers 5GB of email storage, up to 1000 emails per day, custom email domain names, and up to five email address aliases. The “Visionary” tier costs 24 Euros, US Dollars, or Swiss Francs a month when billed annually, and offers 20GB of email storage, up to 50 email aliases, up to 10 custom email domains, multi-user support, and no limit on how many emails you can send. The visionary tier also includes the visionary tier access to ProtonVPN.
What can’t ProtonMail protect you from
If your device is compromised in some way, there’s no guarantee that any data on your device is safe. The optional auto-lock feature on mobile requires a PIN code or biometric scan to unlock access, potentially protecting you from an attacker with physical access to your device. If someone is able to run code on your device, and you’re signed in, it’s possible for them to access your email. Your best protection against this risk is to follow security best practices to minimise the risk of your device ever being compromised.
ProtonMail can’t protect you from attackers gaining access to your account through guessing or tricking you into revealing the correct password. The only way to protect yourself against this form of attack is to use a long, complex, and unique password and to be vigilant for phishing emails.
Security features
Your emails are all stored in an encrypted format on ProtonMail’s servers using Zero Access encryption, meaning that they have no way to access your email. All emails sent from one ProtonMail account to another are always encrypted at every step of the process. Emails sent to third party email providers are encrypted where possible.
Emails can be further encrypted with a password that you would need to agree with or communicate to the recipient for them to be able to decrypt the message, through a form of PGP. The decryption key can be set to expire after a certain amount of time, after which the message becomes unreadable forever.
ProtonMail’s servers are located in a guarded former nuclear bunker in the Swiss Alps under a kilometre of granite, making it almost infeasible for any attacker to ever be able to gain unauthorised access to the infrastructure. This should also help to indicate how much the company values security and privacy, on top of the Swiss reputation for being champions of privacy and security.
ProtonMail’s security features and stance make it ideal for anyone with privacy concerns about traditional email providers, or anyone wanting to communicate sensitive information, such as companies with data security requirements, or journalists living under oppressive regimes. The Zero Access encryption means that ProtonMail can never hand over specific email data, however, under Swiss law they can be forced to hand over metadata, including IP addresses, when presented with a valid Swiss, and only Swiss, court order.
Tip: Foreign court orders carry no direct weight over ProtonMail. In fact, under Swiss law it is illegal for them to comply, however, the Swiss government can choose to approve the court order, at which point they must comply with or contest the order. This adds a level of protection from abuse from government overreach but still allows cooperation in cases that would be clearly in the public benefit such as helping to prevent imminent terrorist threats. Details of ProtonMail’s history in this regard can be found here.