When testing a website for security issues, one of the main things to keep your eyes open for is user interactions. A user interaction is any action that involves the website processing a form of user action. This can be either in JavaScript on the user’s browser or in interactions with the server, such as with a PHP form. Another source of issues are variables, these don’t need to directly result from user input and instead control another aspect of the page.
Intruder is designed to be a tool to automate the testing of any potential vulnerability source. As with other built-in tools such as Repeater, you can send a request you want to edit to Intruder via the right-click menu. The sent requests will then be visible in the Intruder tab.
Note: Using Burp Suite Intruder on a website for which you do not have permission could be a criminal offence under various computer misuse and hacking laws. Ensure you have permission from the website owner before trying this.
How to use Intruder
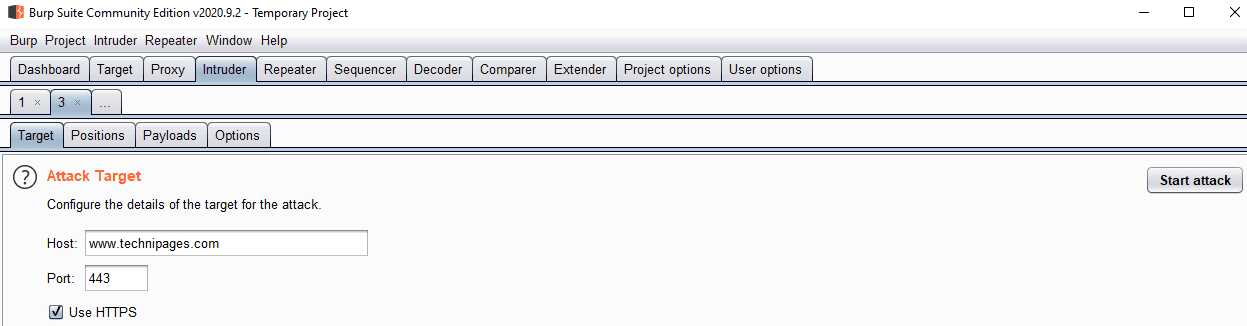
You generally don’t need to configure the “Target” sub-tab in the Intruder tab. If you send a request it automatically populates the values you need to send the request to the right server. It would only really be useful if you want to either manually craft the entire request, or if you want to try disabling HTTPS.
The “Positions” sub-tab is used to select where in the request you want to insert payloads. Burp automatically identifies and highlights as many variables as possible, however, you’ll likely want to narrow the attack down to only one or two insertion points at a time. To clear the selected insertion points, click “Clear §” on the right-hand side. To add insertion points, highlight the area you want to be changed, then click “Add §”.
The attack type dropdown box is used to determine how payloads are delivered. “Sniper” uses a single payload list and targets each insertion point one by one. “Battering ram” uses a single payload list but inserts the payload in all insertion points at once. Pitchfork uses multiple payloads, inserts each one into its respectively numbered insertion point but only ever uses the same numbered entry from each list. “Cluster bomb” uses a similar strategy to pitchfork but tries every combination

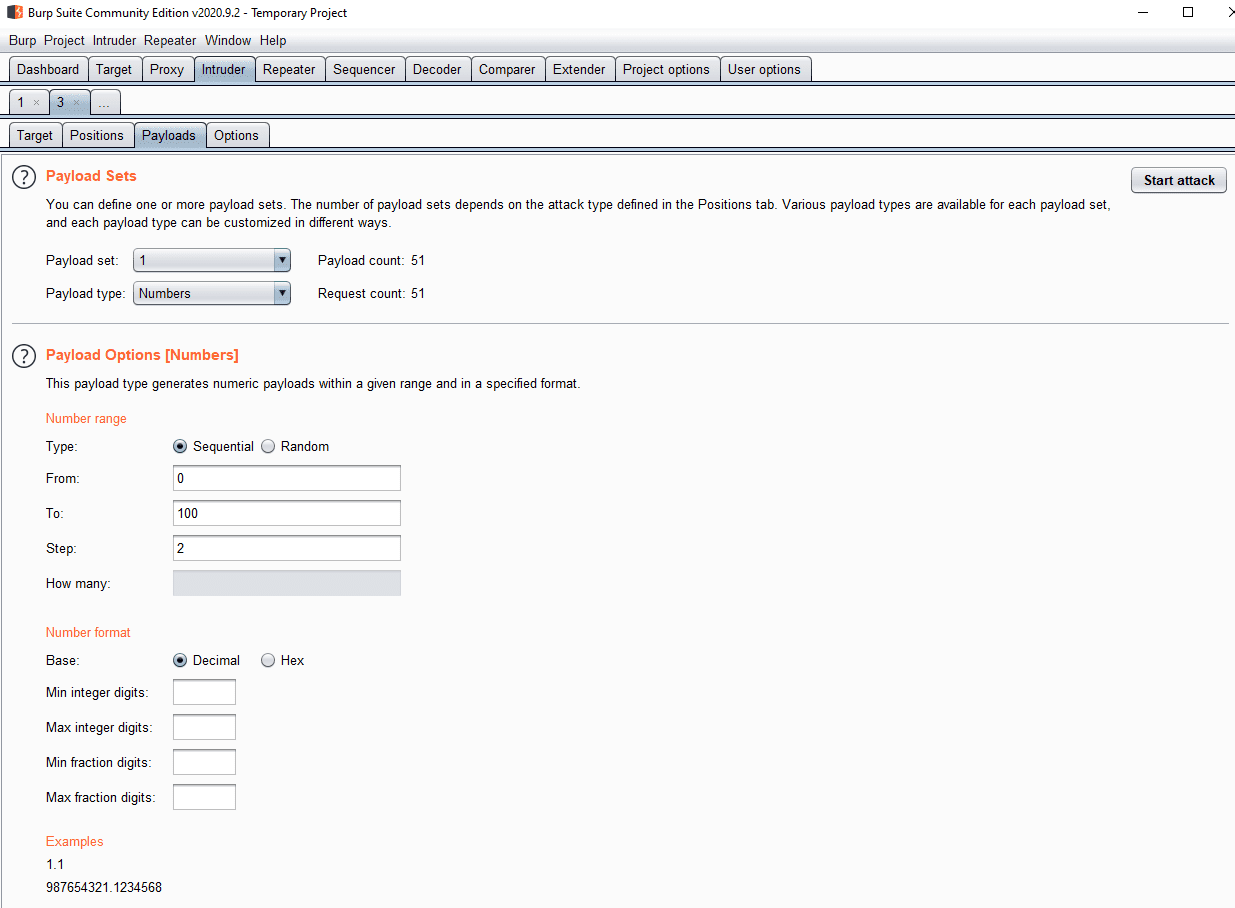
The “Payloads” sub-tab is used to configure the payloads that are attempted. The payload type is used to configure how you specify the payloads. The section below varies depending on the payload type but is always used to specify the payload list values. Payload processing allows you to modify the payloads as they’re being submitted. By default, Intruder URL encodes a number of special characters, you can disable this by unticking the checkbox at the bottom of the page.
The “Options” sub-tab allows you to configure a number of background settings for the scanner. You can add grep-based result matching systems designed to help you identify key information from meaningful results. By default, Intruder doesn’t follow redirections, this can be enabled at the bottom of the sub-tab.

To launch the attack, click “Start attack” in the top-right corner of any of the “Intruder” sub-tabs, the attack will launch in a new window. For the free “Community” edition of Burp, Intruder is heavily rate-limited, while the Professional version runs at full speed.